“Mobile puts the cloud on steroids.” – Steve Van Till, President & CEO, Brivo
Moving physical security to the cloud is Step 1 in the Technology Roadmap Toolkit. Doing so enables new and more efficient ways of collaborating and transforming data into actionable insights. The result: improved organizational configurations, maximized user experience, and improved facility and security operations performance.
We moved our access control and surveillance to the cloud, now what?
IBM asked more than 5,000 C-level executives which technologies they think will be important in the next three to five years. Most CxOs agree that after cloud computing, mobile solutions play a key role.
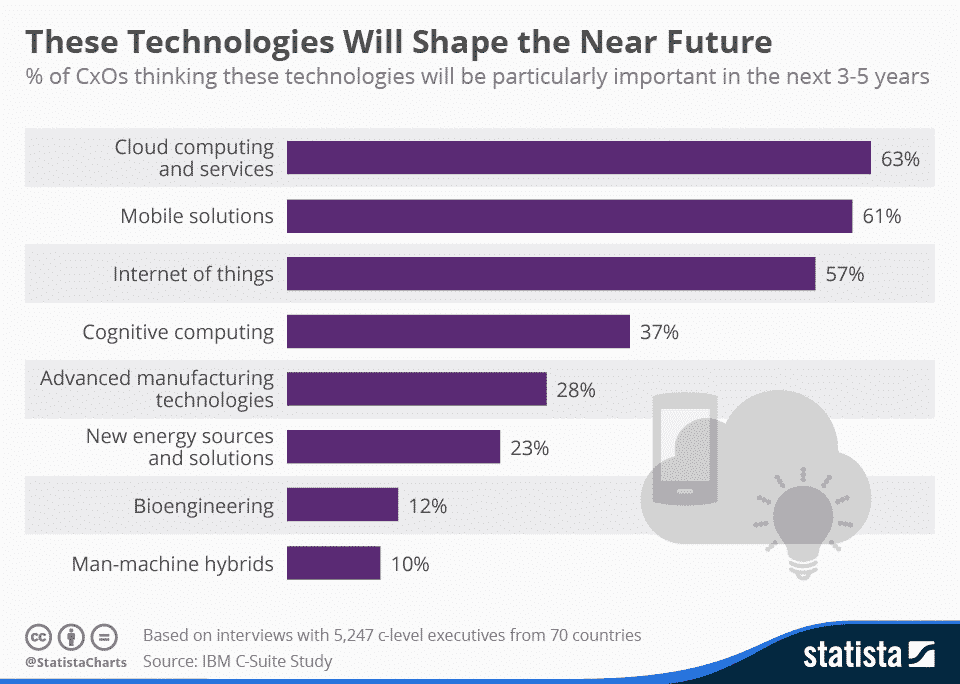
*source: https://www.statista.com/chart/4056/technological-trends/
Mobile technologies will shape the future of physical access control. Its advantages are essential for business operations: access to information at your fingertips, the ability to have a quick emergency response, remote control, and ease of mobile credentials.
It’s fair to say that having a mobile security solution in place is crucial for businesses to succeed in today’s interconnected world.
Now, let’s talk about how mobile technology translates into benefits for security and facility professionals.
Why should facility and security professional adopt mobile?
What’s the opportunity?
It’s interactive security that lets you easily control access to one or multiple facilities with two main benefits:
- Situational awareness: Facility security is complicated. It is rapidly evolving and requires professionals to plan for a diverse set of scenarios- from intrusion to active shooters, theft, and fraud. In the face of such daunting security challenges, you need true situational awareness.Mobile security applications combine security and operational activities into a mobile view that organizes physical security data and offers real-time management. This provides users real-time information about the facility thereby reducing costs, optimizing revenue, and increasing efficiency.
- Mobile credentials: When you use smartphones as keys to grant access to your facilities, you can also take advantage of these additional benefits:
- Mass notification: Enable active notification capabilities to your users.
- Location awareness: Grant access based on location restrictions.
- Revoking a credential: Remotely remove users’ credentials and related applications connected to the corporate network.
- Multi-factor authentication (MFA): Allow administrators to require a screen unlock pin/biometric/gesture to set up a mobile credential without the addition of new door hardware.
Watch our webinar, 5 Innovative Ways To Manage Physical Security, to learn how mobile adoption helped the modern workspace company, Beather, make facility management secure, efficient, and rapidly scalable.
What’s at stake?
Outdated technology slows your business down. If you don’t innovate, you run the risk of losing productivity and, as a result, opportunities. It is easy to put off technology decisions for the more pressing day-to-day matters. Sometimes, “If it ain’t broke; don’t fix it!” can do more harm than good.
Mobile applications for security operations will change the way people perceive the role of security, the value of security, and their relationship to security. It provides flexibility to your users, employees or tenants, and gives the perception that you are up to speed with the latest technology.
Change is also part of the security and facility operation space. Companies that don’t innovate become commoditized. Watch Steve VanTill’s webinar to learn how mobile has penetrated our lives and how to use it in your physical security program.
When should you start looking at mobile applications in building security?
The evidence is overwhelming. We’re moving from the era of desktop Internet access into one where mobile is king. It’s time to put mobile first in your security operations strategy. Adopt a mobile strategy to become more responsive, innovative and agile to build deeper relationships with your customers.
The time to start planning your mobile strategy is now. To get started you must first address that the foundation of any mobile strategy is cloud technology. Mobile applications are only effectively delivered as a cloud service.
![Part 2 [Tool-Kit] Technology Roadmap for building security](https://www.brivo.com/wp-content/uploads/2020/03/Part-2-Tool-Kit-Technology-Roadmap-for-building-security.png)
How do I make my physical security mobile?
Cloud and mobile drive security operations innovation and growth. To get started you need to find an access control solution that already provides mobile technology as part of its services.
What does that mean?
Your access control provider should have applications for both you, the administrator and your users. You should be able to manage access from your mobile device via a mobile application. Your users should be able to use their smartphone as a key to enter your facility, via a mobile application.
If you already have a mobile application for your building or company, choose an access control provider that uses an open API. That means you can integrate access into your existing application – making it a one-stop-shop for your users.
When it comes to mobile applications, creating them for practicality and ease of use is critical. CEO Larry Page articulated it in the New York Times as the “toothbrush test”. It boils down to a simple question: “Is it [the mobile application] something you will use once or twice a day and does it make your life better?” An application that grants your tenants access and independence and one that enables you to manage access to your facility from anywhere, definitely passes the “toothbrush test.”
How can I build a case to adopt a mobile strategy?
Traditional corporate hierarchies are difficult to convince to invest in new security technology. Get executive buy-in on innovative security projects by building a business case. Here is some information to get you started:
- Mobile credentials are essentially more secure.
- Revoking a credential: Remotely remove users’ credentials and related apps connected to the corporate network.
- Multi-factor authentication (MFA): Allow administrators to require a screen unlock pin/biometric/gesture to set up a mobile credential without the addition of new door hardware.
- Mobile credentials increase capabilities.
- Mass notification: Enable active notification capabilities to your users.
- Location awareness: Grant access based on location restrictions.
- Mobile implementation significantly reduces costs.
- Reduction in installation costs: Decrease expenses because no readers are required.
- Real-time facility information: Use facility data to reduce costs, optimize revenue and increase efficiency.
- Mobile offers a better user experience.
- Flexibility: Offer convenience to your users, employees or tenants and give the perception that you are up to speed with the latest technology.
- Responsiveness: Become more innovative and agile, thereby building deeper relationships with your customers.
The future holds more changes to the tools and services you use every day, including the tools you use for facility access control. The security of a door is only as strong as the security of the access credential used to enter it. Put your credential behind the most highly encrypted device you own – your smartphone.
C-suite executives can unlock opportunities for their businesses, improve productivity and become competitive by unleashing the combined power of cloud computing and mobile. It is time to include mobile and cloud in your IT roadmap. Learn more about Brivo’s mobile credentials and applications here.













